Open-source security tools represent a powerful and evolving landscape within the cybersecurity domain. These freely available tools offer a compelling alternative to commercial solutions, providing organizations and individuals with the means to enhance their security posture without significant financial investment. However, understanding their strengths, limitations, and appropriate usage is crucial for effective implementation and leveraging their full potential. This guide explores the diverse world of open-source security tools, covering their various types, applications, and considerations.
From vulnerability scanning and penetration testing to intrusion detection and security information and event management (SIEM), open-source tools offer a wide array of capabilities. This exploration delves into popular tools, best practices, and future trends, equipping readers with the knowledge to effectively utilize these resources in building robust security frameworks. We’ll examine both the advantages – like cost-effectiveness and community support – and the disadvantages – such as potential lack of dedicated support and the need for technical expertise – to provide a balanced perspective.
Defining Open-Source Security Tools
Open-source security tools represent a significant segment of the cybersecurity landscape, offering a compelling alternative to commercially licensed software. These tools are developed and maintained collaboratively by a community of developers, researchers, and security professionals, making them freely available for use, modification, and distribution under various open-source licenses. This collaborative nature fosters transparency, rapid innovation, and a robust ecosystem of support and improvement.
Open-source security tools provide a range of functionalities designed to detect, prevent, and mitigate security threats. Their accessibility and flexibility make them attractive options for organizations of all sizes, from small businesses to large enterprises. However, it’s crucial to understand both their advantages and disadvantages before implementing them.
Advantages and Disadvantages of Open-Source Security Tools
Compared to commercial alternatives, open-source security tools offer several key advantages. Firstly, the cost is significantly lower, often eliminating the need for expensive licensing fees. Secondly, the source code is publicly available, allowing for thorough examination and customization to meet specific organizational needs. This transparency also allows for quicker identification and remediation of vulnerabilities. Thirdly, a vibrant community often surrounds these tools, providing a wealth of support, documentation, and continuous improvement through updates and patches.
However, open-source tools also have some drawbacks. Support might be less structured compared to commercial products, relying heavily on community forums and online resources. The level of technical expertise required for installation, configuration, and maintenance can be higher. Furthermore, while the source code is open, ensuring its security and reliability requires careful vetting and verification, as vulnerabilities could potentially exist undetected. Finally, the lack of a dedicated support team can impact response times during critical security incidents.
Categories of Open-Source Security Tools
Open-source security tools span a wide range of functionalities, addressing various aspects of cybersecurity. The following table categorizes some common types and provides illustrative examples:
| Category | Description | Example | License |
|---|---|---|---|
| Vulnerability Scanners | Automatically identify security weaknesses in systems and applications. | OpenVAS | GPL |
| Intrusion Detection Systems (IDS) | Monitor network traffic for malicious activity and generate alerts. | Snort | GPL |
| Intrusion Prevention Systems (IPS) | Similar to IDS, but also actively block or mitigate identified threats. | Suricata | GPL |
| Network Security Monitoring (NSM) Tools | Provide comprehensive visibility into network traffic and security events. | Wireshark | GPL |
| Security Information and Event Management (SIEM) Tools | Collect, analyze, and correlate security logs from various sources to detect threats. | Graylog | GPL |
| Penetration Testing Tools | Used by security professionals to simulate attacks and identify vulnerabilities. | Metasploit | GPL |
| Password Managers | Securely store and manage passwords. | Bitwarden | Apache 2.0 |
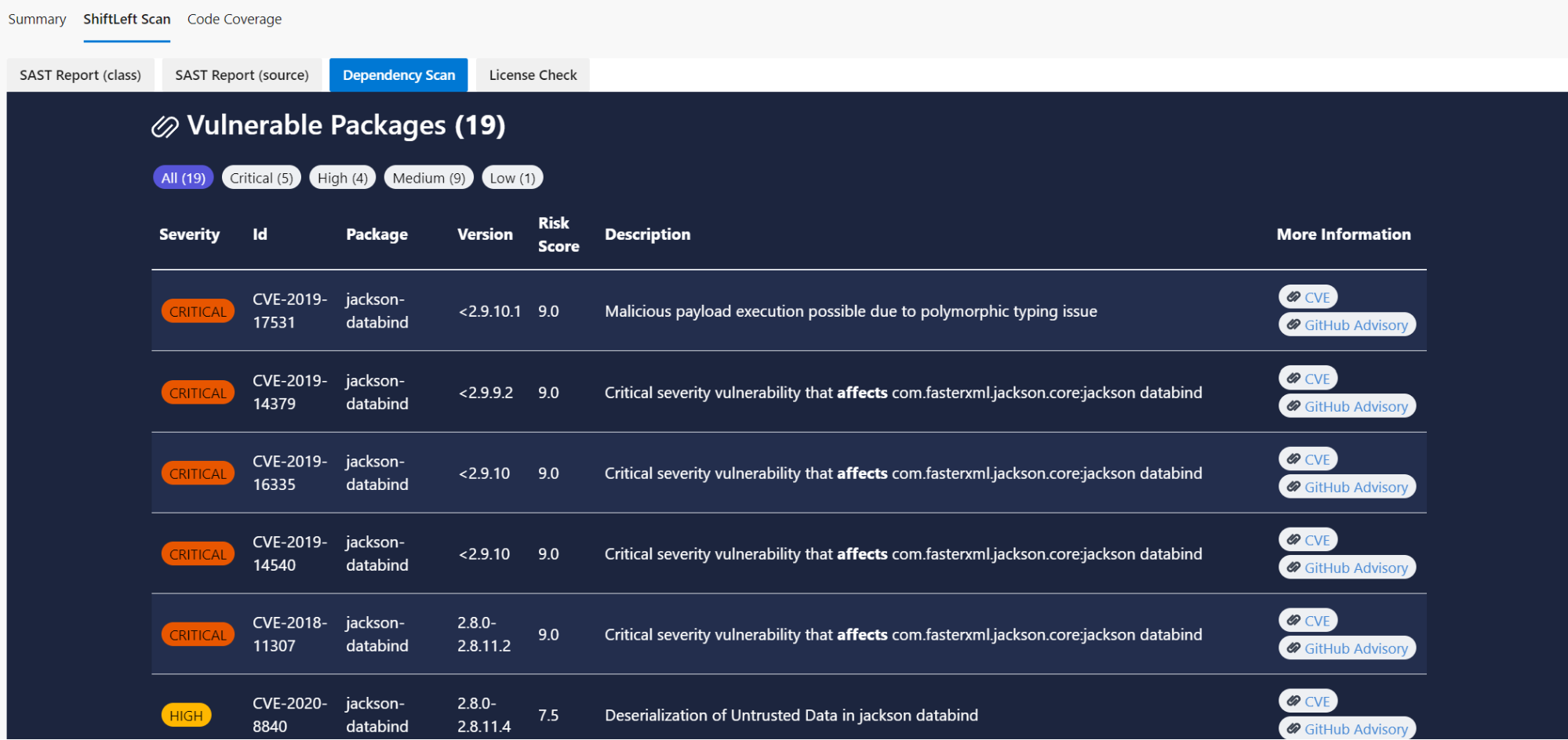
Vulnerability Scanning and Penetration Testing with Open-Source Tools

Open-source tools offer a powerful and cost-effective alternative to commercial security software for identifying and mitigating vulnerabilities. This section explores the process of conducting vulnerability scans and penetration tests using freely available tools, focusing on practical application and result interpretation. Understanding these processes is crucial for bolstering the security posture of any system, regardless of size or complexity.
Vulnerability scanning and penetration testing are distinct but complementary security assessment methods. Vulnerability scanning automatically identifies potential weaknesses in a system, while penetration testing simulates real-world attacks to evaluate the effectiveness of security controls. Both are vital for a comprehensive security audit.
Vulnerability Scanning with OpenVAS, Open-source security tools
OpenVAS is a widely used open-source vulnerability scanner. It works by probing a target system for known vulnerabilities, comparing its configuration and software versions against a database of known exploits. The process involves configuring OpenVAS, defining the target system, initiating the scan, and analyzing the results.
A step-by-step procedure for conducting a vulnerability scan using OpenVAS would involve: First, installing and configuring OpenVAS on a suitable system. This typically involves downloading the necessary packages, setting up the database, and configuring network settings. Second, defining the target system by specifying its IP address or hostname. Third, initiating the scan by selecting the appropriate scan profile. OpenVAS offers various profiles tailored to different system types and security needs. Finally, analyzing the generated report, which lists identified vulnerabilities along with their severity and remediation recommendations. The report should be carefully reviewed to prioritize remediation efforts based on the criticality of the vulnerabilities found.
Penetration Testing with a Suite of Open-Source Tools
A basic penetration test typically involves reconnaissance, vulnerability analysis, exploitation, and post-exploitation activities. While a single tool rarely covers all phases, a combination of tools can effectively simulate a real-world attack. This approach allows for a more comprehensive assessment of a system’s security posture.
A step-by-step procedure for performing a basic penetration test using open-source tools might look like this: First, reconnaissance to gather information about the target system, using tools like Nmap for port scanning and identifying services running on the target. Second, vulnerability analysis, employing tools like Nikto to scan for web server vulnerabilities or OpenVAS for broader system vulnerabilities. Third, exploitation, attempting to exploit identified vulnerabilities using tools like Metasploit (though careful consideration and ethical implications must be addressed before using Metasploit). This step should only be performed with explicit permission from the system owner. Finally, post-exploitation activities, assessing the impact of successful exploitation and determining the extent of potential damage. This may involve privilege escalation attempts or data exfiltration simulations.
Interpreting Vulnerability Scan and Penetration Test Results
Interpreting the results of vulnerability scans and penetration tests requires careful analysis and prioritization. The severity of identified vulnerabilities should be carefully considered, taking into account factors such as the potential impact, exploitability, and the availability of patches or mitigations.
Best practices include: prioritizing vulnerabilities based on their severity and likelihood of exploitation. For instance, critical vulnerabilities with readily available exploits should be addressed immediately. Correlating findings from multiple tools to gain a comprehensive understanding of the overall security posture. Verifying the findings through manual validation to ensure accuracy and avoid false positives. Developing and implementing remediation plans to address identified vulnerabilities, and regularly scheduling vulnerability scans and penetration tests to maintain a strong security posture. Documentation of the entire process, including findings, remediation steps, and any outstanding issues, is essential for ongoing security management.
The realm of open-source security tools presents a dynamic and valuable resource for enhancing cybersecurity. By understanding the diverse range of tools available, their functionalities, and associated best practices, individuals and organizations can significantly strengthen their security posture. While challenges exist, the benefits of cost-effectiveness, community support, and transparency make open-source tools an indispensable asset in the ongoing fight against cyber threats. Continuous learning and adaptation to emerging trends are key to maximizing the effectiveness of these valuable resources.
Open-source security tools offer a cost-effective way to bolster your cloud infrastructure’s defenses. However, remember that improperly configured or underutilized tools can still impact your budget; that’s where careful planning comes into play. For instance, check out these Cloud cost management tips to ensure your security investments align with your overall cloud spending strategy. Ultimately, smart choices with open-source security tools can significantly reduce vulnerabilities without breaking the bank.
Robust open-source security tools are crucial for maintaining data integrity. However, before employing these tools, ensuring your data is clean is paramount; this is where leveraging Data cleansing AI software becomes invaluable. By pre-processing data with AI, open-source security tools can operate more effectively, leading to improved overall security posture.
